Businesses experience a paradigm shift as they enter the age of digital transformation. Conventional models and business processes become inefficient; old communication methods no longer work. Employees get more and more personal gadgets and use them to work out of the office. To ensure productive work regardless of the type of used devices and their location, companies implement cloud applications such as Office 365, Google Apps, Salesforce, Github, Microsoft Azure, Amazon Web Services, etc. Due to these changes, the corporate perimeter becomes blurred or dissolves completely.
Digital transformation and migration of data to cloud services
The leading analytical agencies—Gartner and Forrester Wave—predict that in 2018, the share of clouds in the corporate IT budgets will exceed 45%. By 2020, spendings on SaaS software will grow by 75 B $. There is no way back. The question is whether companies will be able to protect their data in the brave new digital world.
You don’t have to go far to embrace the changes. Just ask yourself a few simple questions. If you have not asked them before, answering them will give you food for thought.
- Which cloud applications are used by the employees of your company?
- How is the use of such applications controlled?
- How do you assess the risk of using these applications?
The need to answer these questions has given rise to a brand new class of security tools, which might soon become a must-have for modern companies.
New approaches to cybersecurity. Cloud Access Security Broker (CASB) solutions
Conventional information protection tools, such as Data Leak Prevention systems (DLPs), Next-Generation Firewalls (NGFWs, UTMs), Intrusion Prevention Systems (IPS), etc. have been initially created to protect the enterprise network perimeter. They are powerless when the security perimeter is blurred, when employees exchange documents via cloud services from mobile phones and laptops from anywhere. However, there is a specialized technology that remedies this weakness: Cloud Access Security Broker (CASB).
Shadow IT are IT solutions that are not controlled by the IT Department. Almost all cloud applications can be referred to Shadow IT because corporate employees use various services without the engagement of IT staff. The Shadow IT resources are not necessarily malicious: business units often use cloud services for legitimate purposes, i.e., increasing team productivity. The key to user and data protection is to ensure the visibility of cloud applications used in the company.
Most companies believe that their employees use about ten cloud applications, but actually, their number can exceed one hundred. The technology giants such as Amazon, Microsoft, Google, Adobe, Salesforce, VMware, etc. have an earnest approach to security. However, there are also other services developed by young companies, which are very convenient for business but do not provide adequate protection. The development paradigm of such vendors is grow fast or die slow, and their task is to give the users a convenient and fully-functional service. They put all their effort into adding new features or optimizing the user interface while forgetting about security concerns. The most widely encountered risks are:
- Insecure storage of user data and credentials at the vendor’s side
- Unreliable account, roles, and access management
- Vulnerabilities in the cloud service provider infrastructure, lack of state-of-the-art security tools
- Using vulnerable technologies during application development
Some of the key CASB functions are detecting all cloud services used in the company, assessing the risks related to their use, and assisting in blocking the most vulnerable ones. However, these are far from all their capabilities, and in the next section, we will tell you about the less-known ones.
Four pillars of CASB
CASB capabilities can be conventionally divided into four main categories:
- Cloud service audit
- Data security
- Vulnerability analysis
- Compliance with regulatory and corporate standards
Cloud service audit
Visibility of corporate cloud services is a strategic business task. Conventional network security features such as proxies, firewalls, and DNS logs can only provide basic information. However, only a dedicated CASB solution can provide full visibility and detailed analysis of more than 10,000 applications used in today's world.
Why do you need visibility and analysis of your cloud applications?
- To detect Shadow IT. This function helps IT specialists to understand which cloud applications are used and who uses them.
- To identify potentially dangerous cloud applications. Security officers can detect vulnerable and malicious cloud applications and add them to the company's blacklist.
- To block and permit access to cloud services. After getting the full picture, IT specialists can apply access policies to allow access to helpful cloud services and prohibit dangerous applications.
- To ensure compliance with regulatory requirements. Security officers can monitor cloud services and put them in compliance with regulatory requirements.
Data security
CASB solutions can protect data in cloud services. They have the tools to manage access to specific services from individual devices and support differentiation of access rights to critical data. Many hi-end CASB solutions have a built-in User and Entity Behavior Analytics (UEBA) system that proactively reveals suspicious activities.
Besides, CASB can classify data, operating like a DLP for the cloud that detects and analyzes storage and transfer of confidential data. Advanced data leak protection can be provided by the integration of CASB with third-party DLP systems.
Finally, CASB allows you to anonymize and encrypt sensitive data sent to clouds. It is possible to use various algorithms of full or selective encryption.
Threat protection
Enterprise-class cloud applications are well-protected. The main cyberattack vector is to compromise user credentials and thus gain access to data. Afterward, intruders will be able to distribute malware and make targeted attacks on corporate infrastructure.
CASB has built-in threat protection and prevention capabilities, such as behavioral analysis, antivirus scanning, detection of behavior patterns based on machine learning methods, and real-time analysis of threats from cloud services.
Compliance with regulatory and corporate requirements
Companies that move even a part of their processes to the cloud need to comply with internal and external standards for personal and corporate data protection. With visibility and control over all cloud applications used by the company, it is possible to assess the current state of cloud security, as well as to use access policies to bring it into compliance.
CASB architecture and operation principle
CASB solutions are most often deployed in the cloud and control the interaction of users and applications through APIs or proxy servers. They also support local and hybrid environments.
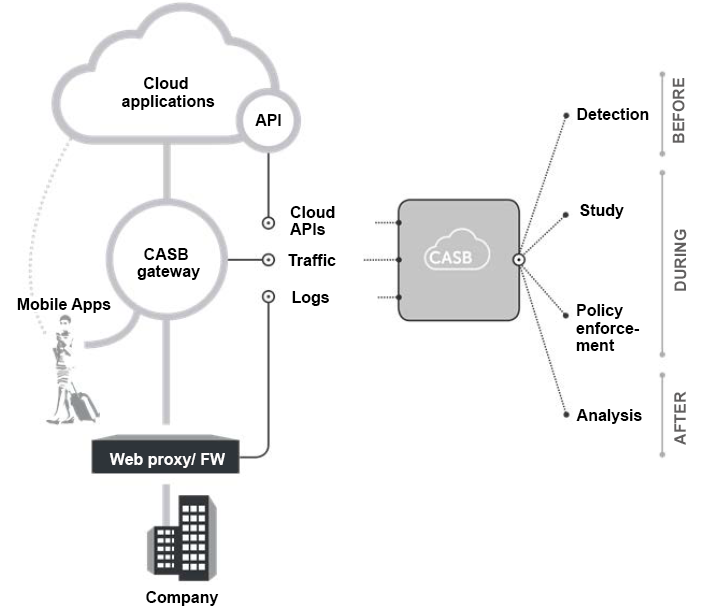
The optimal CASB deployment architecture depends on the customer’s infrastructure and requirements. There is no clear answer about which option is best. However, leading analytical agencies consider the hybrid approach to be the most comprehensive in terms of functionality.
CASB solution market
Almost every large vendor features a solution of this class in its portfolio. The analytical agencies highlight McAfee (Skyhigh Networks), Netskope, and Symantec as market leaders. Cisco, Forcepoint, Microsoft, Oracle, and Palo Alto also have such solutions.
When choosing the most suitable solution for your organization, the following issues should be taken into account:
Cloud application discovery
- How many risk attributes are used to calculate the application security rating? Is it possible to manually assign weights to risk attributes?
- Does the solution generate automatic risk assessment reports?
- Is it possible to block unwanted cloud applications via integration with web proxies or firewalls?
Supported security policies
- Is it possible to configure security policies for both prohibited and allowed applications?
- Does the solution support secure access to cloud services from mobile devices and laptops from beyond the corporate perimeter?
- Is it possible to apply granular context- and content-based policies to user actions based on user name, group, device, location, browser, or user agent?
- Is it possible to apply unified policies across multiple cloud applications?
Deployment
- Is the solution compatible with existing web proxy solutions for maximum protection of your security investment?
- Does the solution support role-based access model?
Data management
- Does the system have DLP functions?
- Can it be integrated with third-party DLP solutions?
- Does it support data classification methods such as regular expressions and contextual analysis?
- Does the solution support tokenization and on-the-fly data encryption during their transfer to, use, and storage in the cloud?
Threat detection
- Does the solution support User and Entity Behavior Analysis (UEBA) to detect suspicious activity?
- Does the solution provide advanced visualization tools to provide an intuitive overview of malicious activity?
- Does the solution support malware detection?
- Can the solution be integrated with third-party Advanced Threat Protection (ATP) solutions?
User experience
- How difficult is the solution to configure and manage?
- Is the user interface intuitive?
- Do end users experience any delays or inconveniences?
- Can users access cloud applications if a CASB solution goes offline?
- How scalable is the solution? How many users and transactions does it support?
Summary
CASB solutions are aimed at protecting data stored in cloud applications. They can detect Shadow IT, control access, traffic, and data operations, and provide actionable insights into the use of permitted and prohibited cloud services. CASB solutions prevent data breaches, analyze user behavior patterns, and are capable of anonymizing and encrypting transferred information. They can also protect your company against malware and unauthorized access.
The global CASB market is at its dawn, but it already has clear leaders, the products from which have the richest functionality. Russian vendors have not released their solutions of this class yet, but some products are expected to see the light in 2019. The booming interest in cloud services both from developers and users is obvious, so we can anticipate that CASB solutions will become a top trend in the Russian market.
References:
- An Executive Guide by Eric Andrews, Gerry Grealish, Rehan Jalil
- https://www.anti-malware.ru/analytics/Market_Analysis/cloud-access-security-broker
- https://www.gartner.com/it-glossary/cloud-access-security-brokers-casbs/
- https://www.esecurityplanet.com/products/top-casb-vendors.html
- https://en.wikipedia.org/wiki/Cloud_access_security_broker









